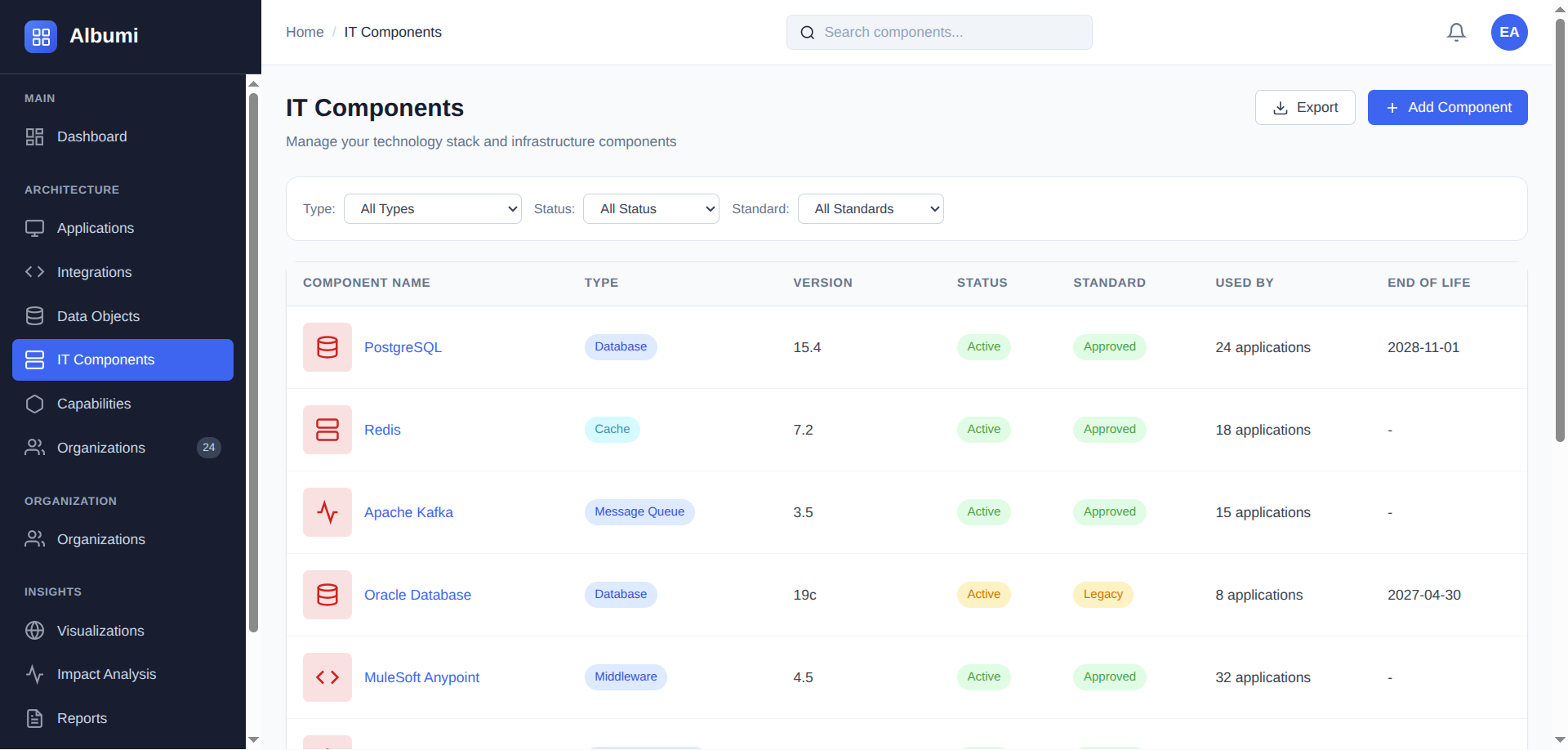
Roles / Security Officer
Security Officer
Core Scenario
Zero-Day Vulnerability Response
Log4j-style emergency? Find all affected systems in seconds, prioritize by exposure, and coordinate patching immediately.
- Find IT component with vulnerable versions
- List all applications using those versions
- Prioritize by external exposure and data sensitivity
- Generate emergency patching list with owners
Exposure Report: "23 apps with Log4j, 8 with vulnerable versions, 3 external-facing (P1). Emergency patching initiated."
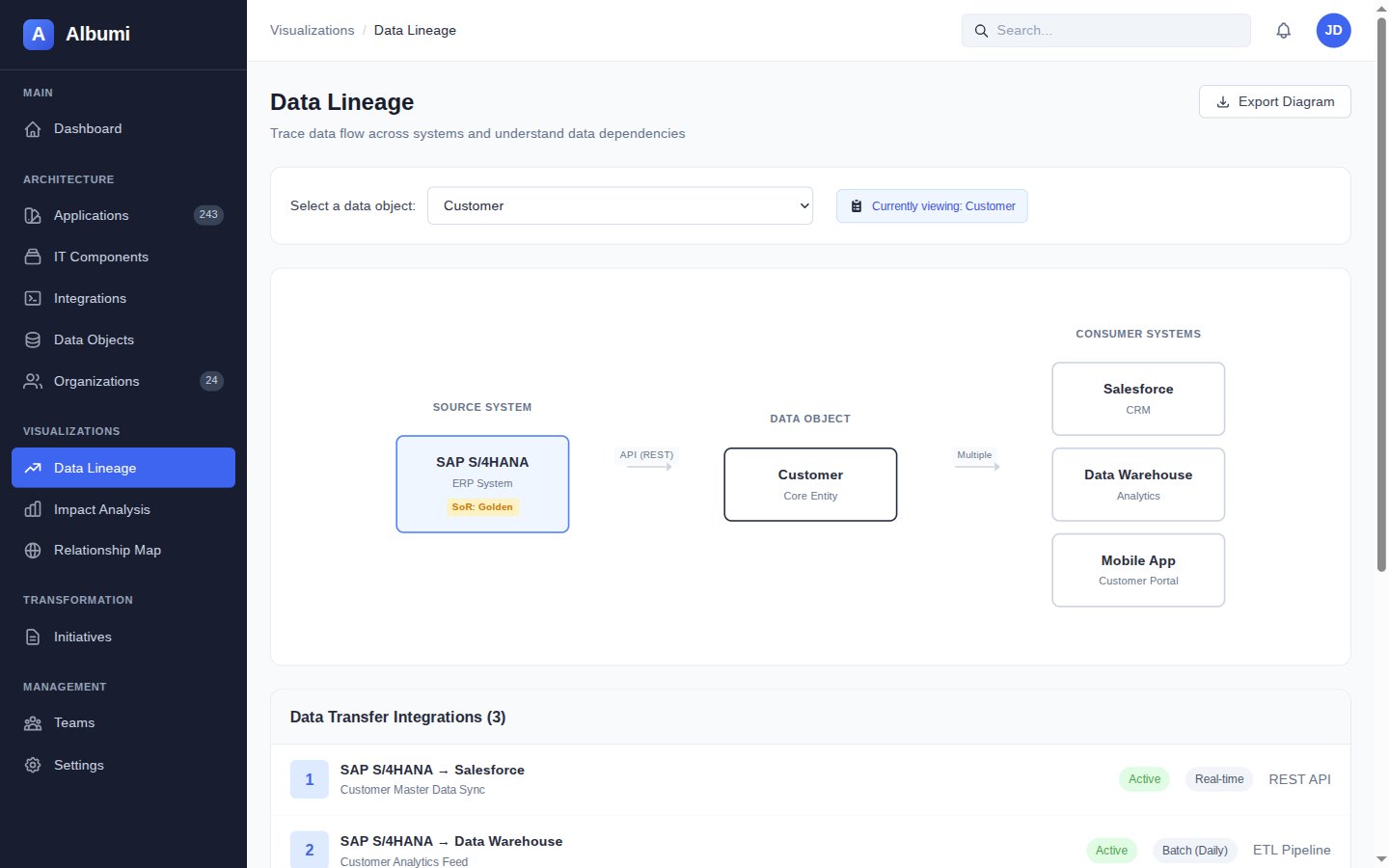
Compliance
PCI DSS Data Flow Mapping
PCI audit incoming? Generate complete documentation of all systems and data flows handling payment card data.
- Find payment-related data objects
- List all systems storing/processing each object
- Find all integrations transmitting payment data
- Export data flow diagram for auditors
PCI Map: "4 systems in scope, 6 integrations, 2 external connections (payment gateway). Diagram ready for audit."
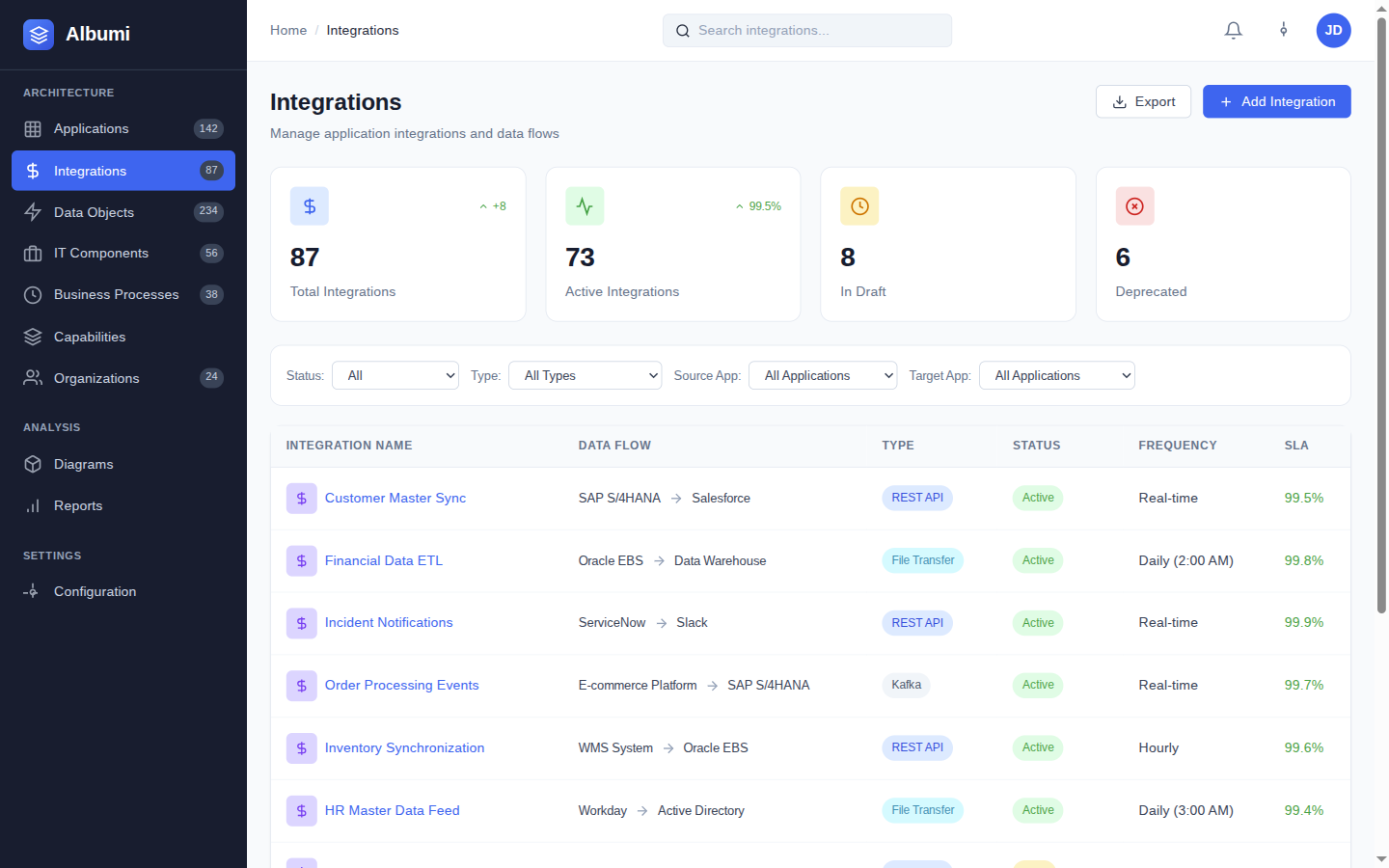
Risk Management
Third-Party Risk Assessment
Vendor security review? See exactly what data leaves your perimeter and to whom — including missing DPAs.
- Filter integrations marked as external
- Check data objects being transmitted
- Identify integrations with PII/sensitive data
- Update third-party risk register
Risk Report: "12 external integrations, 5 with PII, 2 missing DPA (action required). Risk register updated."
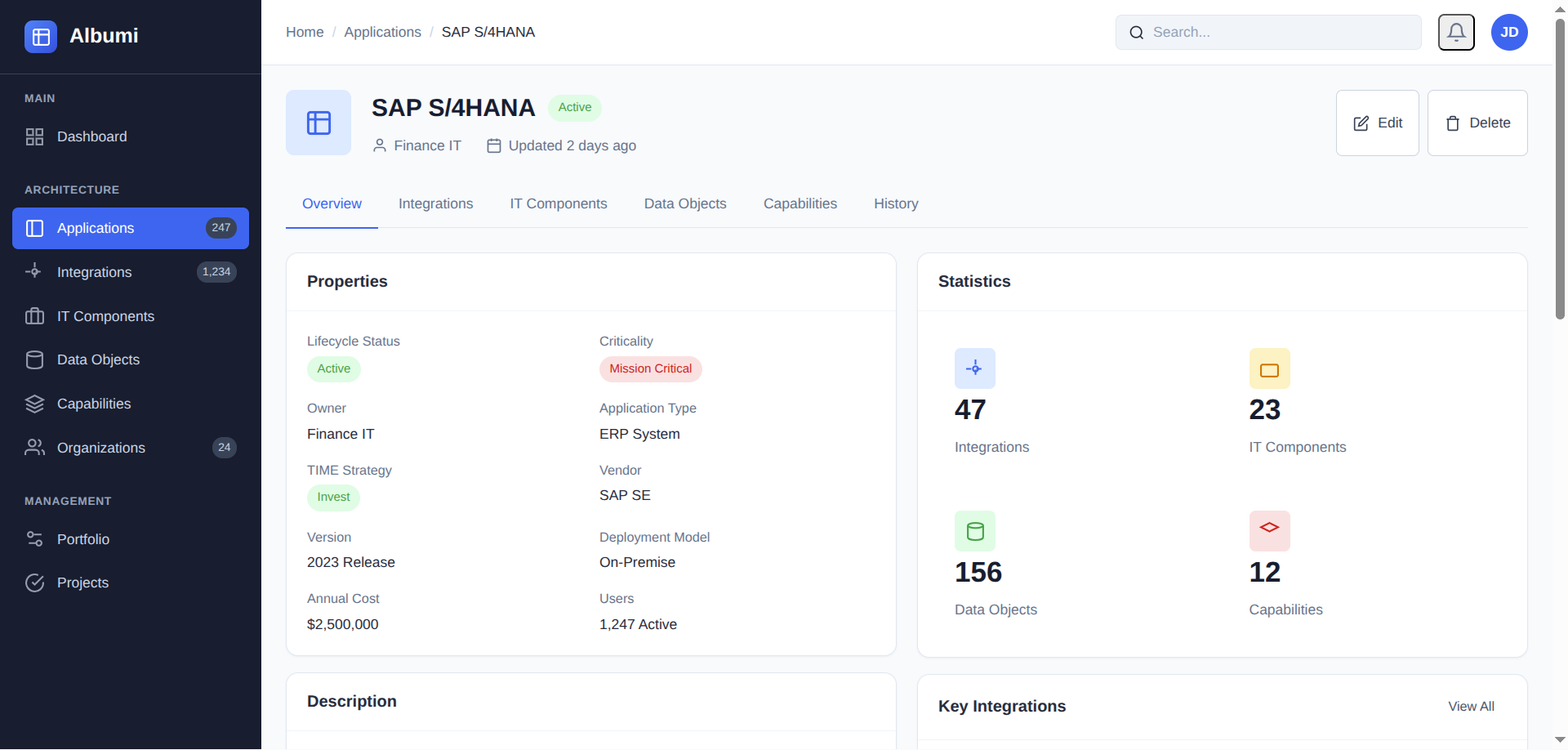
Assessment
New Application Security Assessment
New app going to production? Assess security posture based on data classification, technology stack, and external connections.
- Review data classification (PII, financial, etc.)
- Check technology stack for known vulnerabilities
- Review external integrations
- Generate security findings and recommendations
Assessment: "Handles PII (requires encryption), 2 components need updates, 1 external integration needs DPA. Conditional approval."
Incident Response
Data Breach Investigation
Potential breach detected? Quickly determine what data could be compromised and identify downstream impact.
- Find compromised application
- List all data objects stored/processed
- Check PII flags and data classification
- Trace data sources to estimate affected scope
Breach Scope: "Customer PII (name, email, phone), ~50K records, data sourced from CRM. No downstream propagation confirmed."
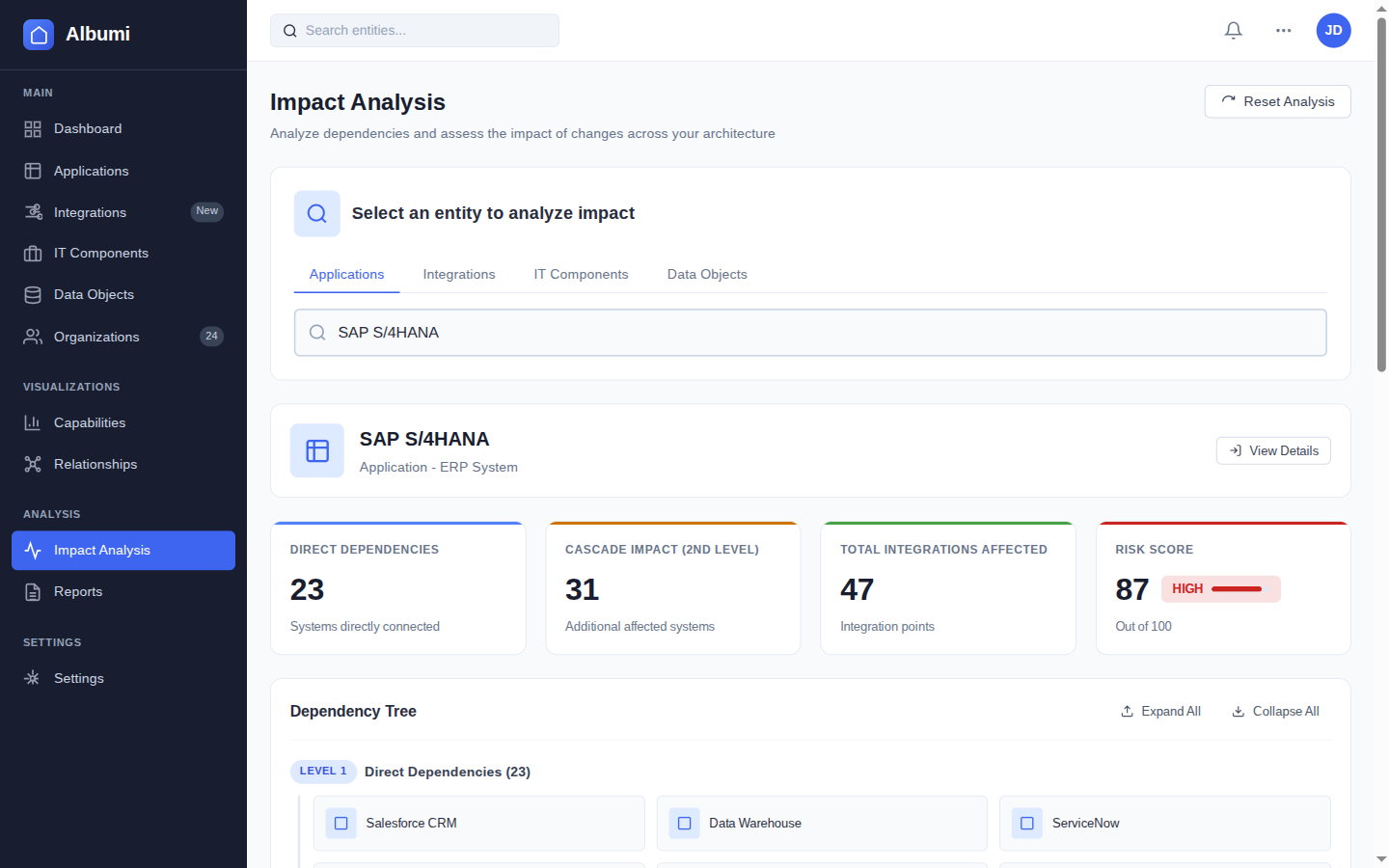
See Albumi in Action for Security Officers
Get a demo showing how to respond to security incidents and manage compliance with complete visibility.
Get Early Access